network segmentation best practices
Expand your Azure partner-to-partner network. Web News Corp is a global diversified media and information services company focused on creating and distributing authoritative and engaging content and other products and services.
 |
| 3 Steps To Develop Your Manufacturing Network Strategy Grantek |
15 Qualities of the Best University Essay Writers.
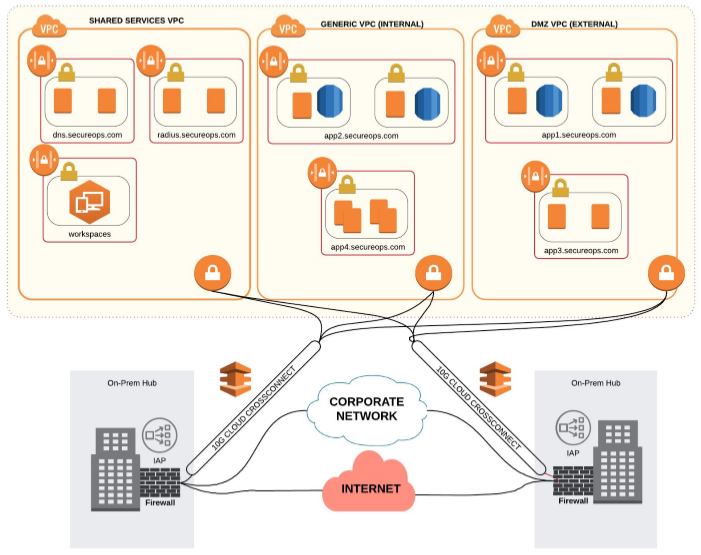
. Accelerate modern app operations with network and security virtualization for WAN data center and cloud. According to our latest data average open rates soar above 80 and click-through rates are around 22-25. Telco Cloud Deliver any application on any cloud anywherefrom the core and the RAN to. Web Find software and development products explore tools and technologies connect with other developers and more.
Web Other standard security best practices also apply including the following. Web Sharing best practices for building any app with NET. The welcome email is the single most effective message you can send. Web Oracle Communications Cloud Native Core Network Slice Selection Function NSSF glibc.
One challenge with this approach is the level of complexity required for successful micro-segmentation. Web Mass General Brigham is honored to have five nationally ranked hospitals based on US. Steps to run the tool. They monitor and control inbound and outbound access across network boundaries in a macro-segmented networkThis applies to both layer 3 routed firewall deployments where the firewall acts as a gateway connecting multiple networks and to.
Find out more about the Microsoft MVP Award. Web Network security best practices. Navigating media valuation in an expanding media landscape. Best practices and the latest news on Microsoft FastTrack.
News World Report Best Hospitals for 2022-2023. Web Read the scoop from marketing experts on the latest industry trends from Microsoft Advertising. Web Your 1 Best Option for Custom Assignment Service and Extras. The best practice analyzer is built into Windows Server and is available on the server management tool.
If someone enters the wrong email address the. Microsofts best practice analyzer is a tool that checks the DHCP configuration against Microsoft guidelines. Web These network security best practices will help you build strong cybersecurity defenses against hackers to protect your network from compromise. Web Six tips and best practices to drive better ROI outcomes.
CISA and MS-ISAC are distributing this guide to inform and enhance network defense and reduce exposure to a ransomware attack. Suggested Firewall Security Zone Segmentation. Welcome emails also help keep your list clean and improve your email deliverability. In the above illustration we have used firewall security zone segmentation to keep servers.
Media valuation is increasingly layered and nuanced. Bringing IT Pros together through In-Person Virtual events. Read more about our rankings 1 in Hospital Medical Research. 3 budgeting strategies to boost media ROI.
Sign up to manage your products. The patch for this issue will address the vulnerability only if the WLS instance is using JDK 170_191 or later or JDK 180_181 or later. Educate users about security. 7 Network Segmentation Segregation Best Practices.
Web The CVSS score assumes that the software passes data received over a network directly to Outside In Technology code but if data is not received over a network the CVSS score may be lower. Web Microsoft DHCP Best Practices. If done incorrectly it can require a significant investment to fix and rebuild the entire network architecture which can cause entire organizations to collapse or lead to more security risks. Now we have a basic understanding and overview of network security lets focus on some of the network security best practices you should be following.
Web NAT Best Practices. AFS was a file system and sharing platform that allowed users to access and distribute stored content. We have outlined these and firewall DMZ best practices below. When using both dynamic and static NAT the ACL that sets the rule for dynamic NAT should exclude the static local hosts so there is no overlap.
For example you might have a zone for sales a zone for technical. Discover tips and trainings for your small or medium business. Web 11 Security Practices to Manage Container Lifecycle. Use firewalls and antimalware.
Firewalls are a vital tool for applying zero trust security principles. Web Andrew File System AFS ended service on January 1 2021. Professional Case Study Writing Help. Oracle Communications Cloud Native Core Security Edge Protection Proxy.
Run DHCP Best Practice Analyzer. Perform a network audit. Web But the fact that attackers were apparently able to leverage their third-party access to reach Targets payment systems suggests those practices were improperly implemented -- at best he said. Beware of using ACL for NAT with permit ip any any as you can get unpredictable results.
ROI data can help. Web Best practices for securing your data operating systems and network How monitoring and alerting can help you achieve your security objectives This whitepaper discusses security best practices in these areas at a high level. It does not provide how-to configuration guidance. As Close to 100 As You Will Ever Be.
Web On September 30 2020 a joint Ransomware Guide was released which is a customer centered one-stop resource with best practices and ways to prevent protect andor respond to a ransomware attack. Web Single-Machine Model Parallel Best Practices Learn how to implement model parallel a distributed training technique which splits a single model onto different GPUs rather than replicating the entire model on each GPU. Ensure secure remote access via VPNs zero-trust network access or Secure Access Service Edge. Web Top 8 Best Network Segmentation Practices.
The first step to secure a network is to perform a thorough audit to identify the weakness in the network posture and design. Keep up to date with current security threats. AFS was available at afsmsuedu an. Web SDN segmentation.
Change any default credentials. A more modern approach to segmentation applies an SDN-automated network overlay. Suggested Firewall Security Zone Segmentation. CVE-2022-23219 CVE-2021-38604 CVE-2021-43396 and CVE-2022-23218.
Web However there are network segmentation best practices that should be followed. Plan your Firewall Deployment. Network segmentation involves segregating the network into logical or functional units called zones. Here are the best.
These are the NAT best practices. 9 Promises from a Badass Essay Writing Service. Implementing network segmentation can be a costly and time-consuming practice. For service specific configuration guidance.
Keep software patched and up to date. Get recommended practices for DevSecOps teams that desire a more modern app methodology. Finding the 1010 Perfect Cheap Paper Writing Services. Are there any NAT best practices.
 |
| Network Segmentation Security Best Practices Forescout |
 |
| Interview Tufin S Cto On Network Segmentation And How To Avoid Being The Next Target |
 |
| Network Segmentation Best Practices |
 |
| Network Infrastructure Design With Segmentation And Traffic Management |
 |
| Plan For Landing Zone Network Segmentation Cloud Adoption Framework Microsoft Learn |
Posting Komentar untuk "network segmentation best practices"